🚩babyshell
Notes
Online Shellcode Assembler/Disassembler
The catflag C Wrapper
catflag C Wrapper// catflag.c
void main()
{
sendfile(1, open("/flag", 0), 0, 1000);
}gcc catflag.c -o \;Writing Shellcode
Method 1: Pwntools (Connor's Method)
Method 2: Manually (Yan's Method)
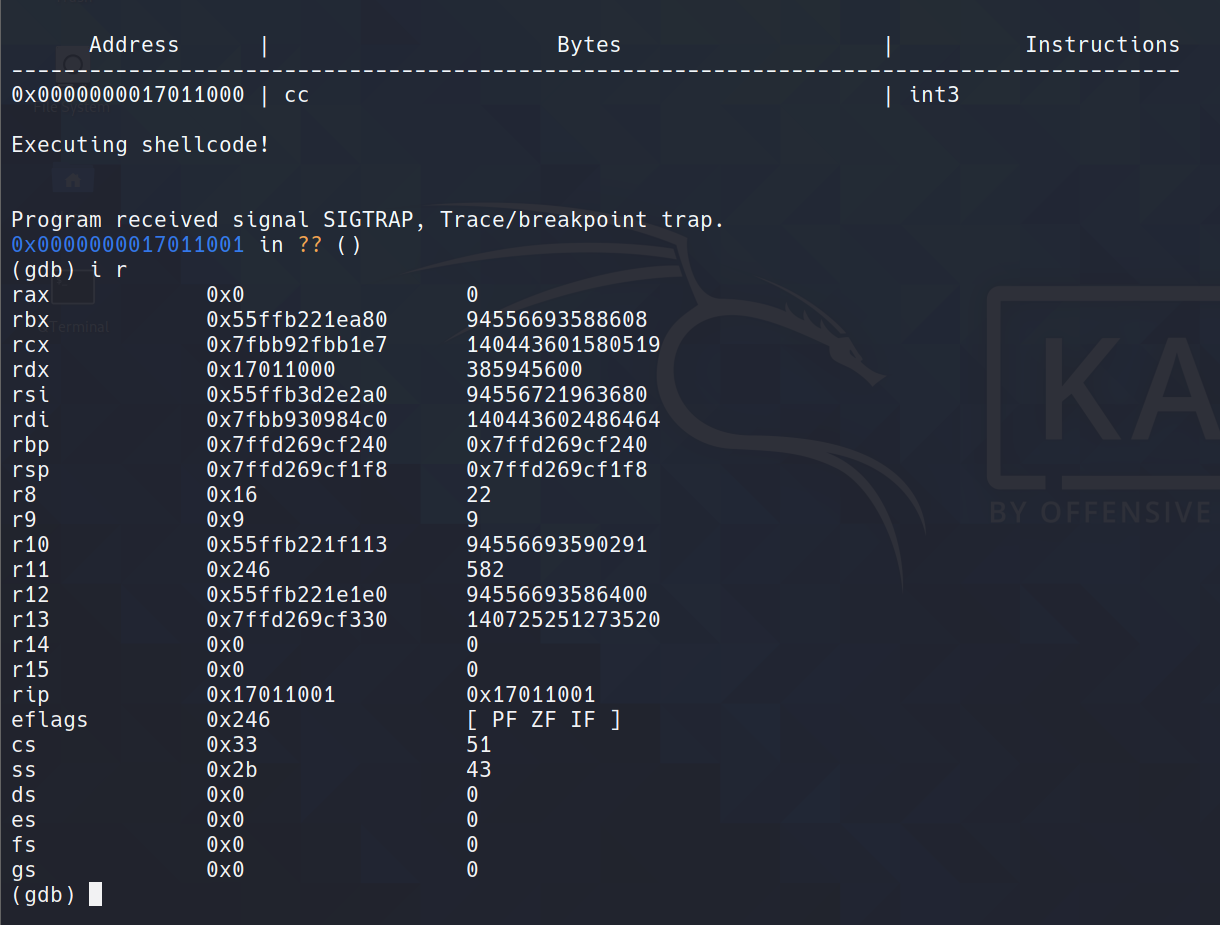
Breakpoint
Utilizing Register States
Level 1
Challenge
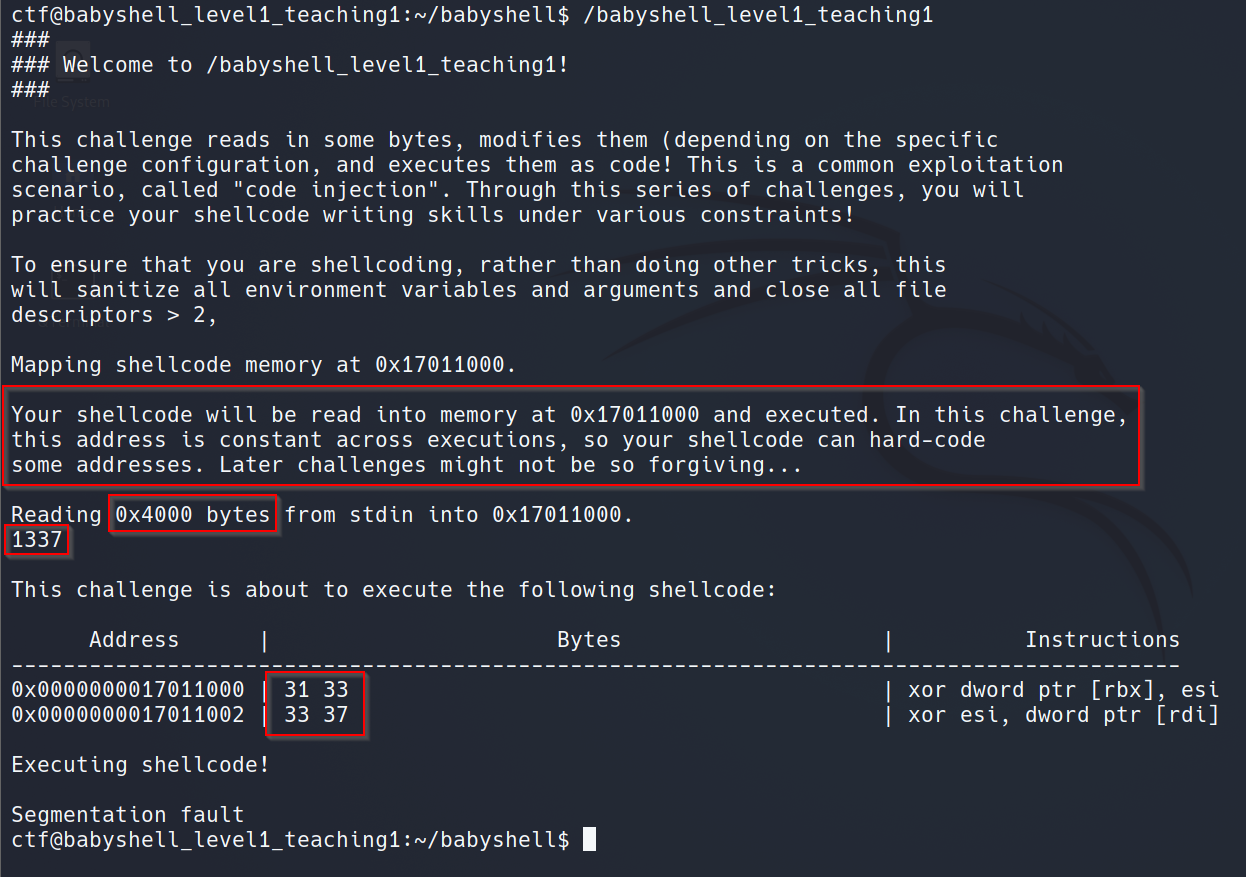
Solution
Exploit
Level 2
Challenge
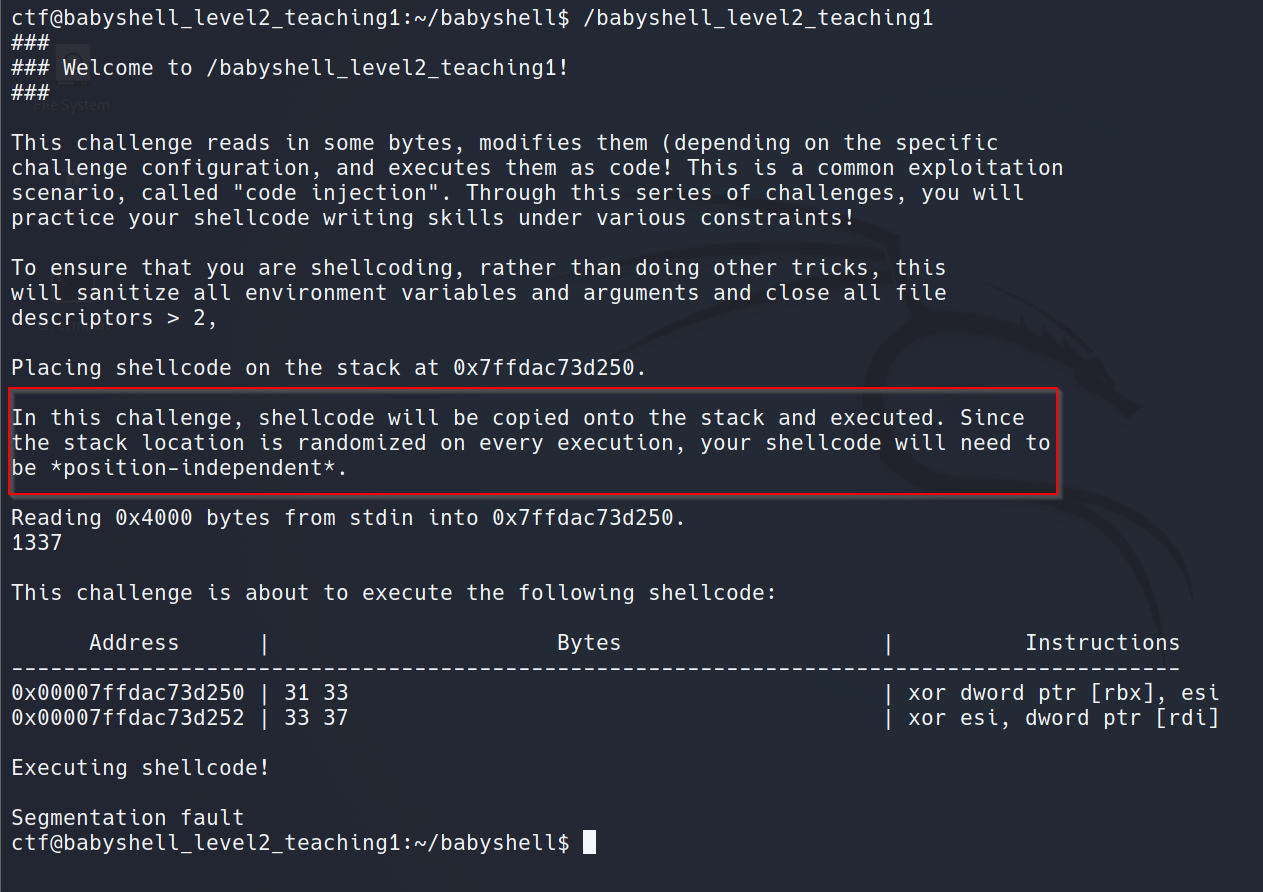
Solution
Exploit
Last updated