✅Brainfuck (Insane)
Summary
In the enumeration phase, we investigate the SSL certificate and learn two DNS names. One name points to a WordPress site and the other points to a "secret forum".
We run WPScan and find a vulnerable plugin. Exploiting this vulnerability, we gain access to the WordPress Admin panel without knowing the password.
The admin panel contains a SMTP password, and we can get access to the emails using Evolution. The credential for the "secret forum" is in one of the emails.
In the "secret forum", we encounter an "encrypted" thread and we have to figure out a way to decrypt the ciphertexts. Once all the messages are decrypted, we get a download link for an encrypted RSA key. We need crack the password out of it using John. At this stage, we can SSH in as Orestis and get the user flag.
In the privilege escalation phase, we are given a simple RSA encryption script and the objective is RSA decryption. The output is the root flag.
Skills Learned
Enumerating SSL certificates
Exploiting WordPress
Exploit modification
Enumerating mail servers
Decoding Vigenere ciphers
SSH key brute forcing
RSA decryption techniques
IP
RHOST: 10.129.1.1
LHOST: 10.10.14.60
Nmap

Intuition tells us to investigate port 443.
SSL Certificate Enumeration
Visiting https://10.129.1.1 gives us a blank nginx page:

Click the "lock" icon and investigate the SSL certificate:

First, we get an email address orestis@brainfuck.htb:

Next, we get two DNS names www.brainfuck.htb and sup3rs3cr3t.brainfuck.htb:

Now we should add 10.129.1.1 brainfuck.htb www.brainfuck.htb sup3rs3cr3t.brainfuck.htb to /etc/hosts and visit https://brainfuck.htb, https://www.brainfuck.htb, and https://sup3rs3cr3t.brainfuck.htb to see if there is any valid page. It turns out that https://brainfuck.htb and https://www.brainfuck.htb point to a WordPress site:

And https://sup3rs3cr3t.brainfuck.htb points to "Super Secret Forum":

WPScan
When we see a WordPress site, usually we want to run WPScan in the background using the command wpscan --url https://brainfuck.htb --disable-tls-checks. In this case, WPScan finds an outdated plugin named wp-support-plus-responsive-ticket-system:
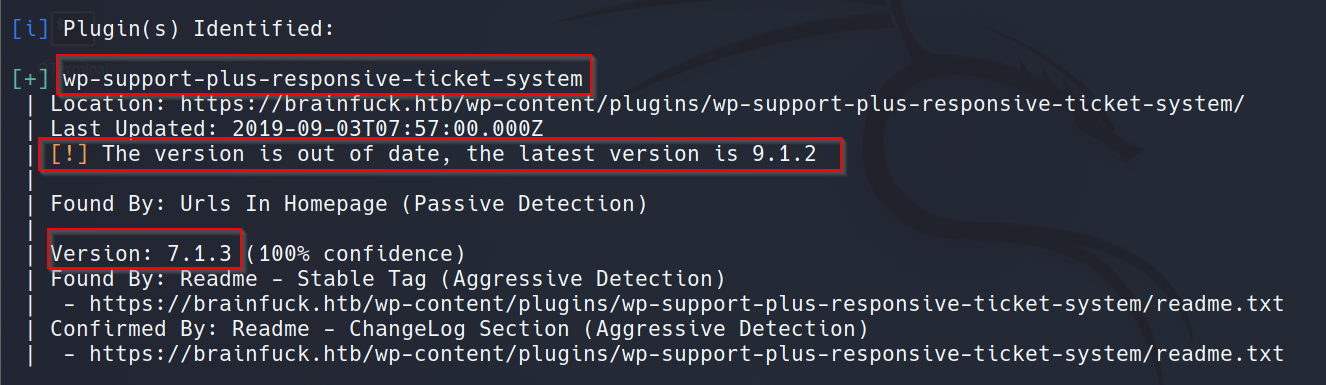
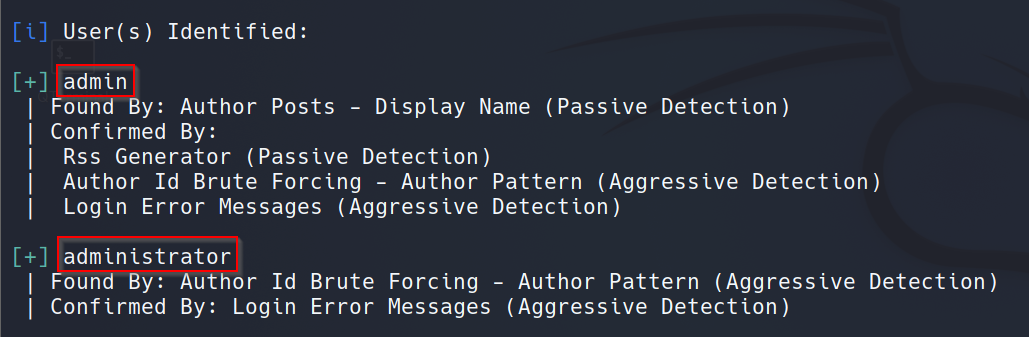
We can also enumerate the usernames using WPScan. The command is wpscan --url https://brainfuck.htb --disable-tls-checks --enumerate u. WPScan finds two usernames admin and administrator:
WP Support Plus Responsive Ticket System 7.1.3 Privilege Escalation
Searching this plugin on Google leads us to ExploitDB 41006 at https://www.exploit-db.com/exploits/41006. It suggests that we can log in to admin panel without knowing any password using the PoC HTML file. We need to modify the "action" attribute to "https://brainfuck.htb/wp-admin/admin-ajax.php". Also, the administrator user is a low-privilege user and the admin user is what we want. The final PoC HTML content is:
What we want to do here is saving this HTML code as PoC.html and run firefox PoC.html. Click "Login". This request will let the server assign an admin cookie for us.
Go back to the WordPress site and refresh the page. Now we have access to the admin panel:

WP Admin Panel => SMTP Password
Enter the admin panel and navigate to "Settings => Easy WP SMTP". There is a hidden SMTP password:

This "hidden" SMTP password can be obtained through developer tools. The password is kHGuERB29DNiNE:

SMTP Login => Forum Credential
We use evolution for SMTP login. Install it:
Open the evolution client:
Go to "File => New => Mail Account" and set up an account with the credential orestis:kHGuERB29DNiNE. The email address is orestis@brainfuck.htb:



The credential for the "secret forum" is in one of the emails:

The credential is orestis:kIEnnfEKJ#9UmdO.
Forum Login => SSH Key
Now we go back to the "secret forum" and log in as orestis:

In the thread "SSH Access", we can learn that Orestis is a really nice person and there is an "encrypted" thread. Also note that Orestis has a "signature template": each thread ends with Orestis - Hacking for fun and profit:

This "signature" will be crucial in the decryption phase. That "encrypted" thread is just "Key". Note that Orestis's signature is encrypted as three different ciphertexts:

This is the behavior of Vigenère cipher. From dcode.fr, we obtain the Vigenère cipher key:

The key is fuckmybrain. Once we have the key, we can decrypt each ciphertext. The crucial message contains a download link to the SSH key:

Just change the IP address and download the SSH key:
Foothold: Encrypted SSH Key
Here is the content of the id_rsa file:
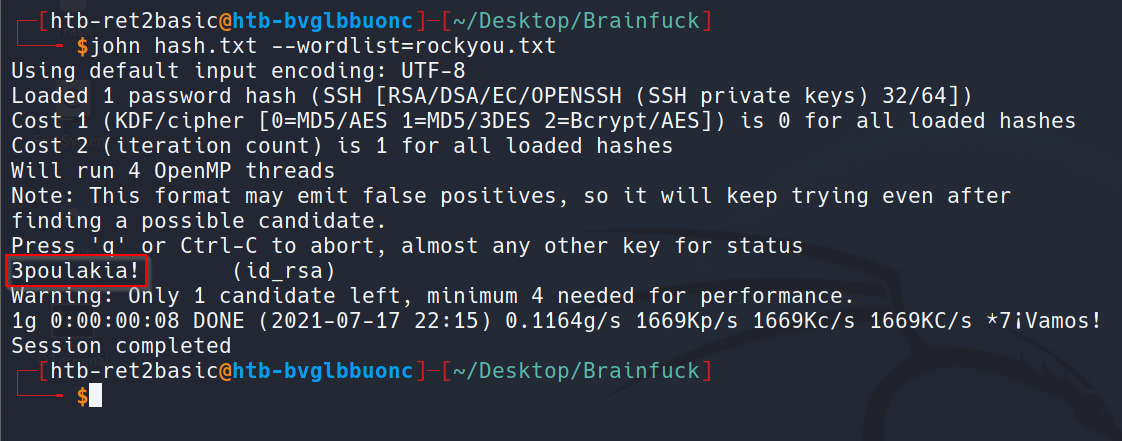
Note that this SSH private key is encrypted and we need to brute-force the password. This password will be used when we SSH in as Orestis. First, we need to do ssh2john to convert the format. We use ssh2john.py:
Next, crack the hash with John:
The password is 3poulakia!:
Now SSH in as Orestis:
We are Orestis:

Privilege Escalation: RSA Decryption
The encrypt.sage file contains the source code for RSA encryption:
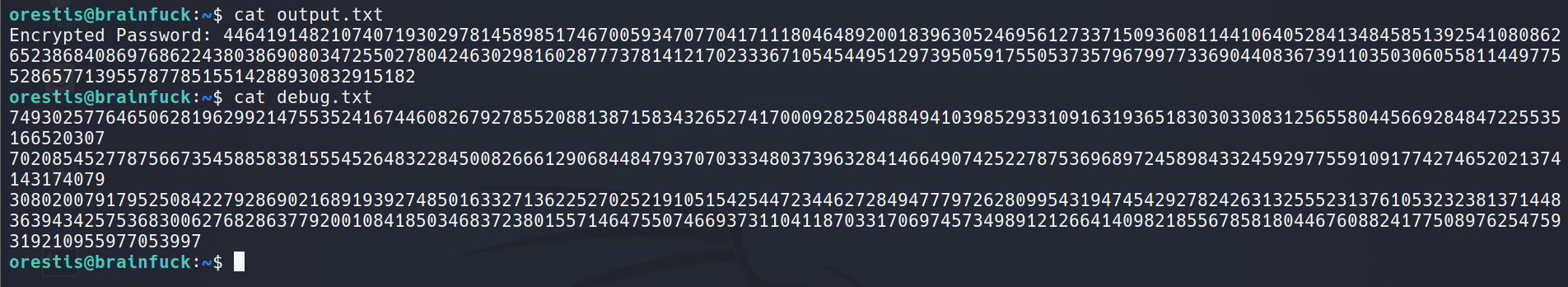
The root flag /root/root.txt is encrypted using this script and our object is to decrypt it. This challenge is trivial since $p$, $q$, and $e$ are stored in debug.txt:
Write a simple decryption script locally:
The output is just the root flag.
Last updated