Web Exploitation
{"authors": ["y4y", "ret2basic"]}
Ancient History (Chrome DevTools)
Solved by ret2basic
Challenge
I must have been sleep hacking or something, I don't remember visiting all of these sites... http://mercury.picoctf.net:52731/ (try a couple different browsers if it's not working right)
Solution
Search for "history" in source code:

GET aHEAD (HTTP HEAD Method)
Solved by ret2basic
Challenge
Find the flag being held on this server to get ahead of the competition http://mercury.picoctf.net:21939/
Solution
Change the HTTP method to HEAD:

Cookies (Cookie Editor)
Solved by ret2basic
Challenge
Who doesn't love cookies? Try to figure out the best one. http://mercury.picoctf.net:17781/
Solution
Enter "snickerdoodle" in the searching box and now we are redirected to /check:

We are assigned a cookie name=0. Change this cookie to name=1, name=2, and so on. Eventually the flag is shown when name=18:

Scavenger Hunt (Common Files)
Solved by ret2basic
Challenge
There is some interesting information hidden around this site http://mercury.picoctf.net:44070/. Can you find it?
Solution
Flag is divided into 5 parts:
View source code.
Examine
mycss.css.Examine
/robots.txt.Examine
/.htaccess.Examine
/.DS_Store.
Who are you? (HTTP Request Methods)
Solved by ret2basic
Challenge
Let me in. Let me iiiiiiinnnnnnnnnnnnnnnnnnnn http://mercury.picoctf.net:1270/
Solution
The challenge says:

Step 1
Set User-Agent: PicoBrowser to satisfy the browser requirement:

Step 2
Set Referer: http://mercury.picoctf.net:1270/ to satisfy the same-site requirement:

Step 3
Set Date: Wed, 21 Oct 2018 07:28:00 GMT to satisfy the date requirement:

Step 4
Set DNT: 1 to satisfy the Do-Not-Track requirement:

Step 5
Set X-Forwarded-For: 31.44.224.128 to satisfy the geographic location requirement:

Step 6
Set Accept-Language: en-US,en;q=0.9, sv to satisfy the language requirement:

Some Assembly Required 1 (WebAssembly)
Solved by y4y
Challenge
http://mercury.picoctf.net:55336/index.html
Solution
View source code:

The JavaScript code G82XCw5CX3.js is obfuscated. Deobfuscate it with JS Nice:
Note that there is a part of the URI in the array _0x402c:

Here ./JIFxzHyW8W should be some file located in the root directory. Download this file:
It turns out that this file is a WebAssembly binary. The flag can be extracted with strings:

More Cookies ()
Someone, solve it!
Challenge
I forgot Cookies can Be modified Client-side, so now I decided to encrypt them! http://mercury.picoctf.net:10868/
Solution
Todo!
It is My Birthday (PDF MD5 Collision)
Solved by ret2basic
Challenge
I sent out 2 invitations to all of my friends for my birthday! I'll know if they get stolen because the two invites look similar, and they even have the same md5 hash, but they are slightly different! You wouldn't believe how long it took me to find a collision. Anyway, see if you're invited by submitting 2 PDFs to my website. http://mercury.picoctf.net:11590/
Solution
Corkami has an amazing writeup on all kinds of collisions on Github. For this challenge, simply use poeMD5_A.pdf and poeMD5_B.pdf:

Once the check is passed, we are given the PHP source code together with the flag:
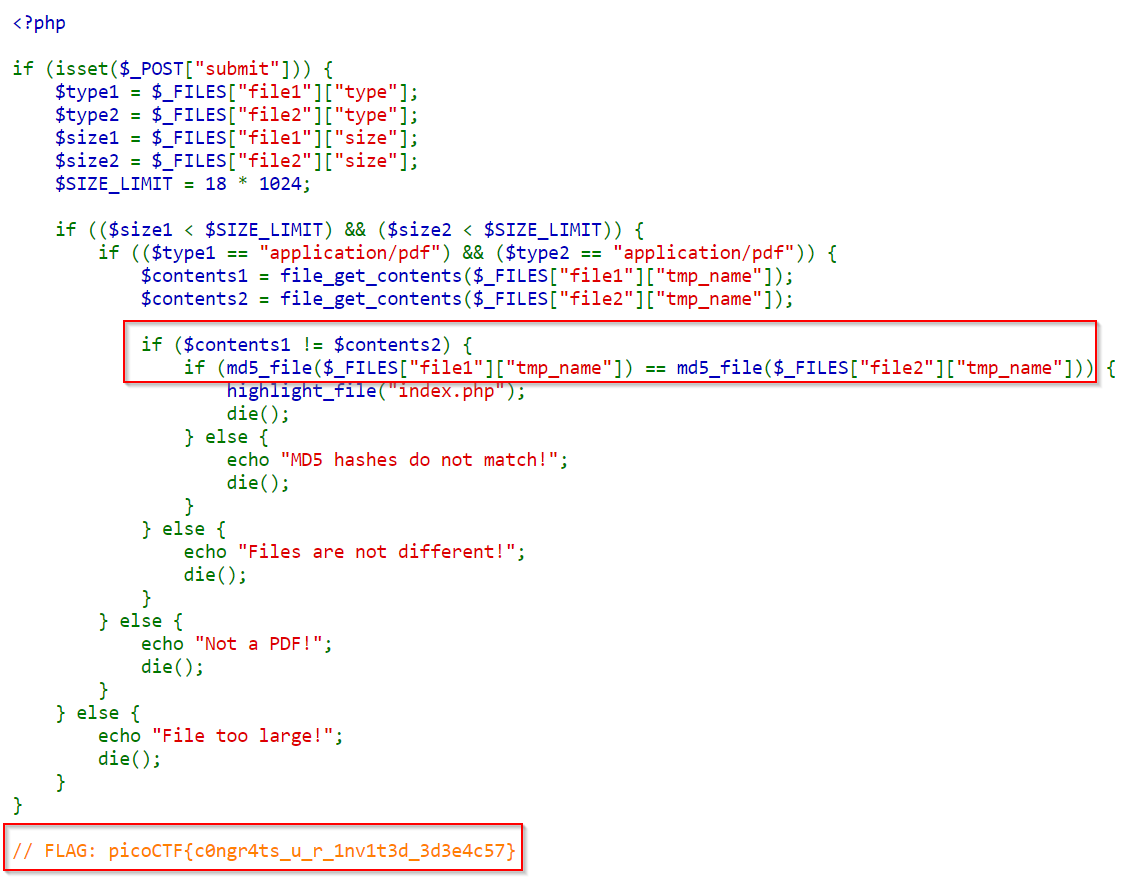
The source code checks if the uploaded pdfs are different but with the same MD5 hash. This check is not sufficient anymore due to PDF MD5 collision.
Some Assembly Required 2 (WebAssembly)
Solved by ret2basic
Challenge
http://mercury.picoctf.net:61778/index.html
Solution
This level won't be as easy as Some Assembly Require 1. To learn more about WebAssembly Text Format, read Understanding WebAssembly text format.
Same story, deobfuscate the Javascript code with JS Nice:
Find the hidden binary in the array _0x6d8f:

Download it:
To decompile the WebAssembly binary, use wabt:
A string that looks like an encrypted flag can be found at the very end of the assembly:
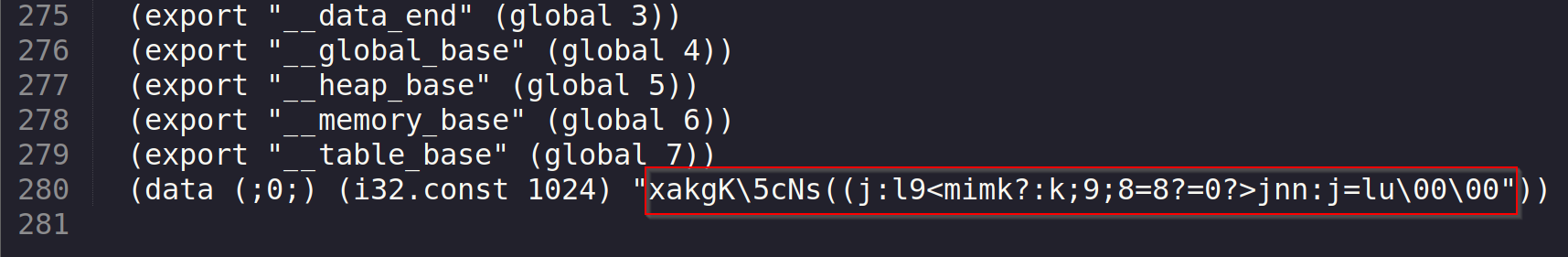
Func 2 is check_flag:
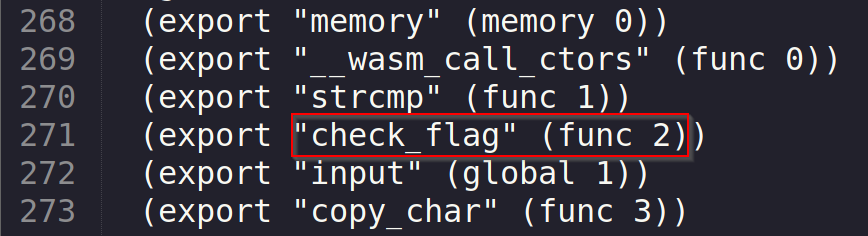
Func 2:
Super Serial (PHP Deserialization)
Solved by ret2basic
Challenge
Try to recover the flag stored on this website http://mercury.picoctf.net:5428/
Source Code
Check robots.txt:

Visiting http://mercury.picoctf.net:5428/admin.phps returns "Not Found", but at least we learn that there are .phps files on the server.
A quick note on .php and .phps:
When you visit a
.phpfile from the browser, the server "runs" the code behind the sceen and returns you the output.When you visit a
.phpsfile from the browser, the server shows you the actual source code.
Although admin.phps does not exist, we could try visiting index.phps to get the source code of the index page:
index.phps:
It tells us the existence of cookie.php and authentication.php. Grab the source code using the same method:
cookie.phps
authentication.phps
Solution
The insecure deserialization is triggered by the unserialize() function in cookie.phps:

The idea is to utilize the access_log class in authentication.phps. This class is supposed to read the access log, but we could let it dump the content of ../flag. The payload object is:
Note from y4y
And what made this attack viable is the die("...".$perm); function call, as well as the __toString() method in the class access_log, __toString tells PHP how the object can be interpretered as string. If you take a closer look, the __toString() in access_log class will return the value of read_log function. Since the access_log class does not have is_admin and is_guest method, it will result an error, and then the die function will print a debug message. Otherwise it would not return anything as file_get_contents simply does not output anything.
Exploit
Most Cookies (Flask Cookie Forgery)
Solved by ret2basic
Challenge
Alright, enough of using my own encryption. Flask session cookies should be plenty secure! server.py http://mercury.picoctf.net:65344/
Source Code
Solution
To learn about how to forge Flask session cookie, read the following article:
The author of this article even built an automation tool named Flask Unsign. We will be using this tool in this challenge.
First, let's identify the vulnerability. The secret key used is predictable:

We could simply brute-force all possible secret keys and see if any of them works.
Examine the session cookie:

This cookie evaluates to {'very_auth': 'blank'}, and our objective is forging a cookie that evaluates to {'very_auth': 'admin'}.
Create cookie.txt:
Create wordlist.txt:
Use Flask Unsign:

Some Assembly Required 3 (WebAssembly)
Someone, solve it!
Challenge
http://mercury.picoctf.net:38541/index.html
Solution
Todo!
Web Gauntlet 2 (SQLite Injection, WAF Bypass)
Solved by y4y
Challenge
This website looks familiar... Log in as admin Site: http://mercury.picoctf.net:61434/ Filter: http://mercury.picoctf.net:61434/filter.php
Solution
Filter: or and true false union like = > < ; -- /* */ admin
This challenge builds upon picoCTF 2020 Mini-Competition Web Gauntlet. Grab the payload and read the explanation.
In that payload we used /**/ (empty comment) to represent space. Note that this challenge does not filter spaces at all. We could simply delete all /**/:
The corresponding SQL query becomes:
Send the payload as username and password can be anything. Send this POST request with burp. This payload also solves Web Gauntlet 3.
Note from ret2basic
An even simpler payload is adm'||'in'%00, where we use || to concatenate strings and %00 (null byte) instead ; to terminate the SQL statement. Check out picoCTF 2020 Mini-Competition Web Gauntlet Round 5.
Source Code
Startup Company (SQLite Injection)
Solved by: y4y
Challenge
Do you want to fund my startup? http://mercury.picoctf.net:44720/
Solution
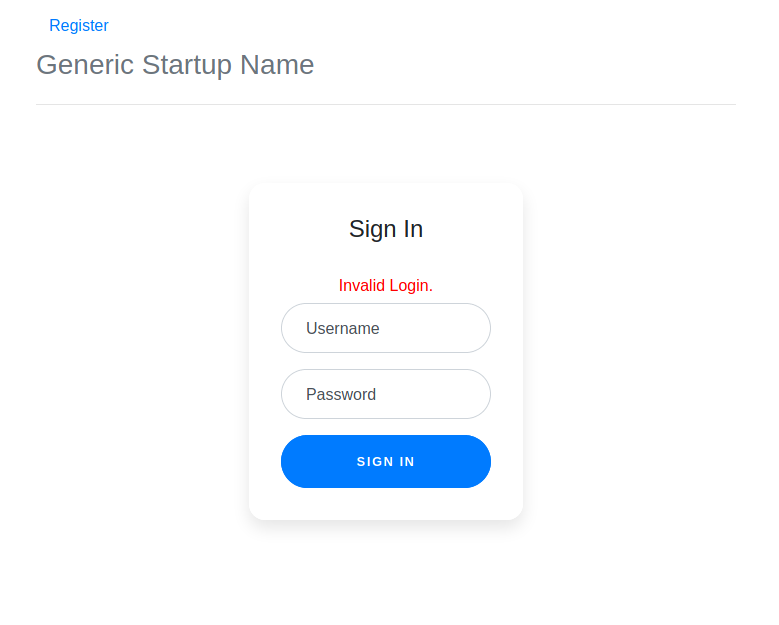
Immediately it asks us to login, and notice the Register on the top left corner? Why the hell not? And spoiler, this isn't part of the actual challenge. Upon loggin in, we see some kind of donation page.
I first tried some letters but apparently it's doing some kind of checking. Since I didn't seem to have any credits so I just entered a huge number, and nothing seemed to happen. Then I tried to intercept the request and realized there is a captcha included in this form. Lucky for us, this captcha is custom generated and not by google.
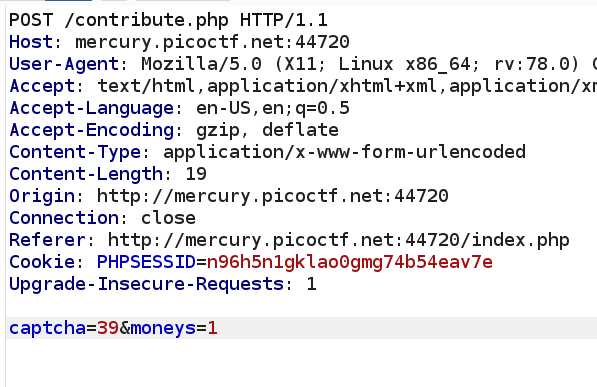
So I tried some basic stuff, like SSTI, Command Injection, and last, SQL Injection. And the last time, the contribute.php returned a database error message.
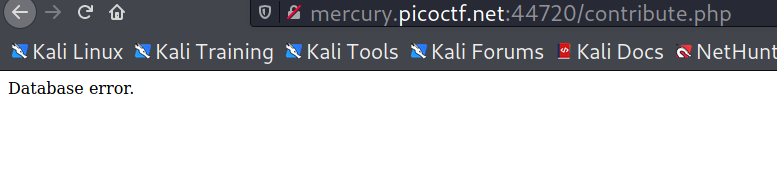
Then I knew I was onto something, and after checking the hints provided by the organizers, I learned the database is SQLite, so I tried some test query like
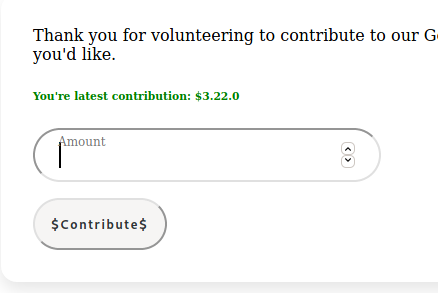
And I knew I definitely didn't donate 3.22.0. The rest is just regular procedure, dump the database and get the flag.
Dump table names:
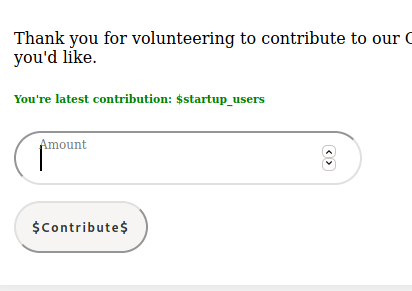
Next, dump column names:
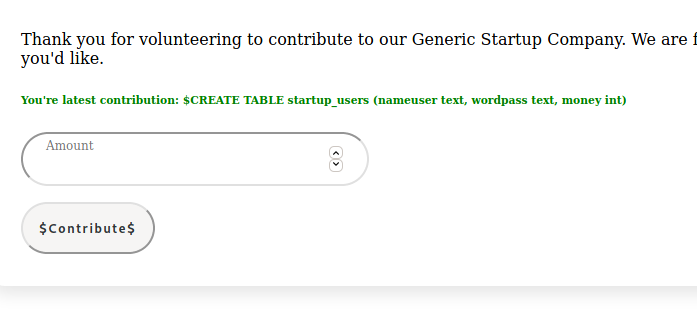
The last part is then to dump the table and see if flag is in there.
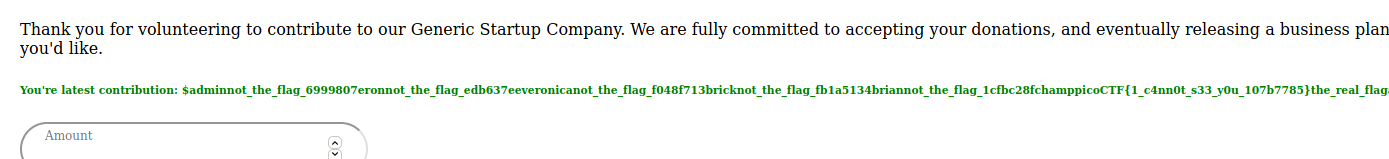
A bit messy, but you can see find the flag in the text.
Some Assembly Required 4 (WebAssembly)
Solved by ret2basic
Challenge
http://mercury.picoctf.net:6755/index.html
Solution
X marks the spot (Blind XPATH Injection)
Solved by y4y
Challenge
Another login you have to bypass. Maybe you can find an injection that works? http://mercury.picoctf.net:53735/
Solution
According to the prompt, we know it's yet another injection problem. And the hint told us that it has something to do with XPATH. Originally I thought this was to use SQL XPATH Error Injection, but later on I realized it was just simply XPATH Injection (From testing functions and stuff).
I could very well be wrong, but XPATH is some kind of query language for XML. After A LOT of research, I finally found some useful function I can use for the injection. Let's talk about them.
count(node) will return how many child nodes does this particular node have. string-length() will return the length of string, you guessed it. local-name() will return the attribute name of the node. substring() does exactly what you expect it to.
To make thing more clear, let's use an example. Here is a sample XML file.
And count(login)=1 because there is only one node of login, and count(user)=2 because there are two user nodes. Then local-name(login)=login as you expected.
Then let's talk about the path in XML files. Like in Linux directories, / means root, so if I want to represent the Alice node, I shall use /login/users/user[1]/, the [1] means the position of node. And of course, the wildcard /* means all of the child nodes.
With those knowledge, we can first try to leak the root node. The payload I used was:
And we can slowly leak the length of root node's name. Then we use the substring() function to dump the name. Rinse and repeat. Eventually we will leak the entire node tree.
I used the exploit below to dump the nodes which mattered. Essentially the structure was like:
And if you are curious about the other stuff, try modify the exploit and dump 'em all. It's gonna take forever, I probably should do a binary search, but meh.
Exploit
Web Gauntlet 3 (SQLite Injection Filters)
Solved by y4y
Challenge
Last time, I promise! Only 25 characters this time. Log in as admin Site: http://mercury.picoctf.net:63504/ Filter: http://mercury.picoctf.net:63504/filter.php
Solution
Use the same payload as in Web Gauntlet 2.
Note from ret2basic
adm'||'in'%00 works as well.
Source Code
Bithug
Someone, pls solve it!
Challenge
Code management software is way too bloated. Try our new lightweight solution, BitHug. Source: distribution.tgz
Solution
Todo!
Last updated